Table of Contents
Information about Lime CRM security update LCSEC18-01
Summary
A vulnerability has been found in Lime CRM Server which, if left unpatched, could allow an attacker having access to a Lime CRM user account to run malicious code on the server running Lime CRM Server.
Technical details regarding this vulnerability can be found here.
Determining if your system is affected
Your Lime CRM installation is affected if:
- You are running an on-premise installation of Lime CRM, i.e. not the cloud offering.
- The installed version of Lime CRM Server is 12.25 - 12.41.1.5.
- The Lime CRM Web Client is enabled.
The Lime CRM Server version can be found either in the Lime CRM Web Client or in the Lime CRM Server Administration (LISA) application:
Version check in Lime CRM Web Client
- Launch your web browser and navigate to Lime CRM.
- When the sign in page appears, click the logo bubble:

- The version number will appear inside the bubble.
Version check in LISA
- Navigate to LISA.
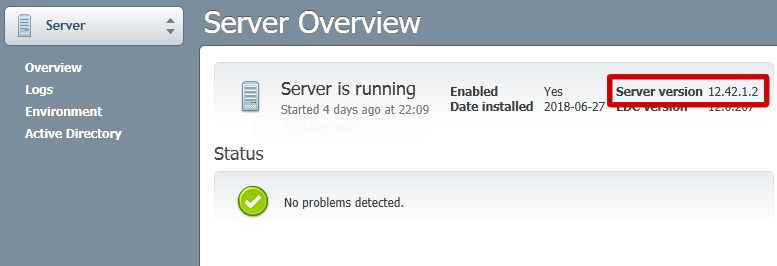
- Look at Server version in the Server Overview section:
Applying the patch
- Download the patch (
lcsec18-01.exe) to the server running Lime CRM Server. - Launch
lcsec18-01.exe. The patch requires administrator privileges to run. - Press OK to begin installation. You will be notified whether the patch was successful or not.
Frequently asked questions
Is it enough to run the patch or do we need to do a full upgrade?
The patch solves only this vulnerability. To benefit from other fixes and new features we always recommend our customers to upgrade as frequently as possible.
Is it critical that we update our installation at once or can we wait a few days/weeks?
Lime recommends that you patch your Lime CRM installation as soon as possible.
Are Lime are aware of any exploits/attacks that utilize this vulnerability?
We are not aware of any such activity whether on-premise or in our cloud based/managed product.
How can I stay up to date with future security announcements?
You may subscribe to the Lime Security Announcements mailing list here.
How will Lime work to make sure this doesn’t happen again? How are you working with secure development? Why wasn’t this found earlier? Etc.
We take security in our products very seriously and do many things to make sure code we write is secure: peer review of all code (at least two pairs of eyes on all code), security training for all employees and dedicated training for developers (next session this autumn). We also do regular security audits and external code reviews with one session planned for this autumn.